Overview
The DragonForce ransomware operation represents the growing convergence of hacktivism and financially motivated cybercrime. Once known for its politically driven campaigns, the group has transformed into a well-organized, profit-oriented Ransomware-as-a-Service (RaaS) enterprise, mirroring broader trends seen across the 2025 ransomware ecosystem. The blog highlights DragonForce’s evolving tactics, from expanding affiliate recruitment and leveraging data leak sites to exploiting high-impact vulnerabilities for initial access. It also explores the group’s technical sophistication, ransom negotiation strategies, and operational structure, offering insights into how modern ransomware collectives balance ideology, profit, and scalability. Overall, the analysis underscores DragonForce’s emergence as a key player in today’s ransomware landscape, blending coordinated cyber operations with a highly adaptive business model.
Key Takeaways:
- Origins and Evolution: The blog traces DragonForce’s transformation from a hacktivist collective to a structured Ransomware-as-a-Service (RaaS) operation.
- Technical Insights: It provides a detailed breakdown of DragonForce’s attack chain, encryption methods, and exploitation techniques.
- MITRE ATT&CK Mapping: The blog aligns DragonForce’s tactics and techniques with the MITRE ATT&CK framework for better defensive understanding.
- Defensive Intelligence: The role of Loginsoft Vulnerability Intelligence (LOVI) is showcased in tracking DragonForce activity and helping organizations strengthen resilience.
What is DragonForce Ransomware?
DragonForce is a profit-driven Ransomware-as-a-Service (RaaS) operation that first emerged in 2023. Originally a pro-Palestine hacktivist group, it quickly evolved into a sophisticated ransomware cartel, recruiting affiliate hackers and other RaaS operators.
This allows affiliates to launch attacks under their own brand while leveraging DragonForce’s infrastructure for malware deployment, leak site hosting, and ransom negotiations. In return, the group takes a 20% share of the profits, enabling rapid growth without conducting every attack themselves.
How DragonForce Ransomware became a global RaaS threat?
DragonForce first appeared in 2023, starting with small ransomware experiments before quickly growing into a fully developed Ransomware-as-a-Service (RaaS) operation. The group promoted itself on underground forums like RAMP, openly seeking affiliates and partners to expand its network and influence.
Its ransomware is based on leaked code from LockBit 3.0 and Conti, giving it a strong base that has since been adapted to attack Windows, Linux, VMware ESXi, BSD, and NAS platforms.
Although driven mainly by profit, DragonForce claims to follow a “moral code,” saying it avoids certain healthcare targets and shows empathy for critical patients, though how strictly this is followed is unclear. Using a double-extortion model (data theft plus file encryption), the group pressures victims during ransom negotiations.
From a new player to a sophisticated, enterprise-style ransomware operation, DragonForce has quickly become a powerful ZXglobal threat.
Affected Countries: United States, Australia, India, New Zealand, Singapore, Canada, United Kingdom, Ireland, France, Spain, Italy, Belgium, Sweden, Switzerland, Czechia, United Arab Emirates, Malaysia, Palau, China, Argentina, Colombia, Curacao, South Africa.

For more details, visit LOVI to explore DragonForce threat profile
Operational and Technical Insights into DragonForce Ransomware
How DragonForce Gains Initial Access
DragonForce ransomware operators use a mix of technical exploits and social engineering to gain access to victim systems. The group also heavily depends on social engineering, including phishing emails, fake SSO portals, SIM swapping, and MFA push "bombing" to harvest credentials often targeting IT help desks to bypass authentication barriers.
Once they get access, the attackers use legitimate accounts to blend in and avoid detection. They combine vulnerability exploits and credential theft to establish a quiet foothold before deploying tools like Cobalt Strike, Mimikatz, and SystemBC.
What are the known vulnerabilities abused by DragonForce Ransomware?
How DragonForce Executes Its Attacks
DragonForce runs malware using Windows commands, DLL hijacking, and PowerShell scripts. They may hide PowerShell commands in registry keys to execute silently at startup. Many attacks also rely on social engineering, like malicious documents with hidden macros or fake PDFs, which start the infection process.
How DragonForce Maintains Persistence on Systems
To stay in the system long-term, DragonForce uses scheduled tasks, system process modifications, registry changes, and valid accounts. This ensures the malware continues running even after the system restarts.
Privilege Escalation techniques used by DragonForce
DragonForce combines credential theft with persistence methods to gain higher system privileges. They employ boot/autostart techniques and registry/scheduled-task modifications to ensure payloads persist across reboots, while relying on stolen or newly created legitimate accounts to retain and elevate privileges. in many intrusions, adversaries also deploy post-exploitation tooling examples include Cobalt Strike and PsExec to escalate privileges, execute commands remotely, and stage further compromise.
How DragonForce evades Detection
DragonForce hides its activity by deleting traces, modifying timestamps, disabling security tools, and even using vulnerable drivers (BYOVD). Indicators include unexpected file deletions, sudden service shutdowns, and installation of unsigned drivers.
Credential theft tactics by DragonForce
The group harvests credentials from Windows memory (LSASS) using tools like Mimikatz or procdump, and targets Active Directory to get domain-wide access. Sometimes credentials are even saved in plaintext files for quick use.
Network Discovery and Reconnaissance by DragonForce
DragonForce maps out victim networks to find high-value systems. They use commands like ipconfig, systeminfo, and WMI and tools like AdFind to gather information on users, groups, and domain trusts. This helps them plan lateral movement and attacks.
Lateral Movement strategies in DragonForce attacks
The attackers move through networks using legitimate admin tools, RDP, SMB. In recent campaigns they abused the SimpleHelp remote management platform, an enterprise-sanctioned RMM gaining remote control that facilitates stealthy propagation across managed service provider networks. Their primary lateral technique remains interactive RDP sessions, leveraging harvested credentials to hop from compromised workstations to file servers and domain controllers, and when needed, enabling RDP or adding accounts to the "Remote Desktop Users" group to create new access paths.
This approach helps them blend in while spreading ransomware and other tools.
How DragonForce collects and exfiltrates data
DragonForce collects user credentials, system info, and network details, storing them for later use in ransomware deployment or extortion.
Command and Control (C2) infrastructure of DragonForce
The group maintains remote control using tunnels, covert C2 channels, and backdoors like Cobalt Strike Beacon. Proxy tools like SystemBC help mask connections, ensuring attackers can maintain access even if one channel is blocked.
Process of exfiltration
Before encrypting files, DragonForce often steals large amounts of data, using SFTP, cloud storage, WebDAV, or command-line tools. Attackers often compress sensitive files into archives and exfiltrate them via SFTP, WebDAV, cloud storage services, anonymous FTP or by using command-line utilities such as rclone or wget to push data to attacker-controlled endpoints. If victims refuse to pay, stolen data is posted on a public leak site as part of a double-extortion scheme.
Impact on targeted systems
DragonForce ransomware encrypts files on Windows, Linux, NAS devices, and VMware ESXi, rendering systems unusable. It uses AES for encryption and RSA for key protection. After encryption, a ransom note (usually README.txt) is dropped, disrupting operations and causing reputational damage.
Ransom Note of DragonForce
DragonForce maintains dedicated dark web leak sites to pressure victims. If ransom demands aren’t met, stolen files are published publicly, increasing regulatory risk and operational disruption. Their double-extortion model gives operators and affiliates strong leverage in negotiations.
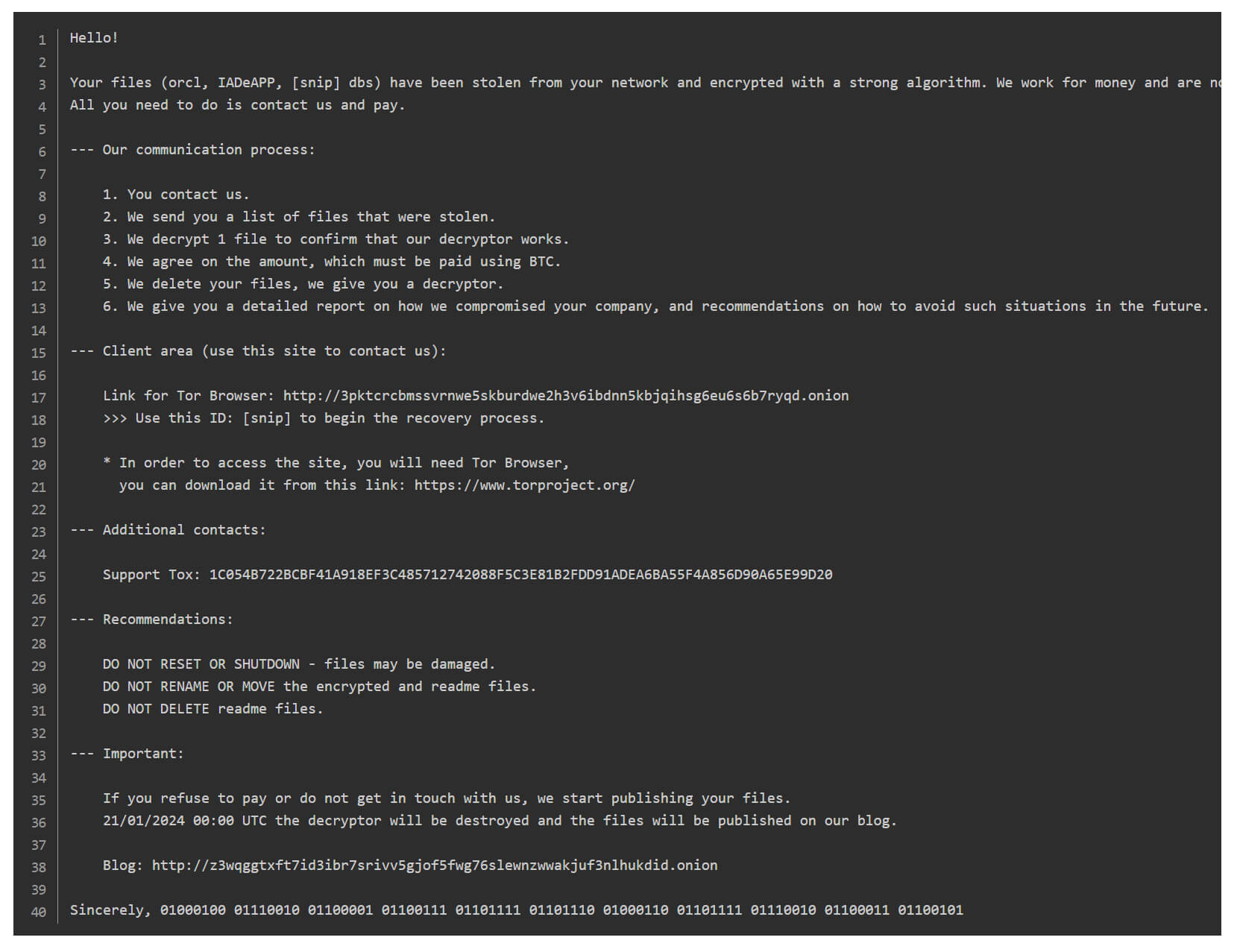
Source: https://www.ransomware.live/group/dragonforce
MITRE ATT&CK Mapping for DragonForce Ransomware
The following table outlines the MITRE ATT&CK tactics and techniques observed in DragonForce ransomware operations, illustrating its methods across various stages of the attack chain.
Mitigation Strategies Against DragonForce Ransomware
- Strengthen Email Security & User Awareness - Deploy advanced filtering to block phishing emails and malicious attachments. Regularly conduct phishing simulations and security awareness training to reduce social engineering risks.
- Timely Patch & Vulnerability Management - Apply security updates without delay, prioritizing critical flaws frequently exploited in ransomware campaigns. Conduct periodic audits to identify and remediate unpatched systems.
- Credential & Authentication Controls - Enforce strong, unique passwords and mandatory rotations. Implement Multi-Factor Authentication (MFA) across all accounts, with strict emphasis on administrative and remote access.
- Remote Access Hardening - Disable RDP if unnecessary; otherwise, restrict it behind VPNs, enforce IP allow-listing, and apply least-privilege access.
- Network Segmentation & Isolation - Separate critical assets such as domain controllers, backup servers, and sensitive databases using VLANs and firewalls to limit lateral movement opportunities.
- Advanced Endpoint Detection & Monitoring - Deploy Endpoint Detection and Response (EDR) solutions tuned to detect post-exploitation tools like Cobalt Strike and Mimikatz. Incorporate behavior-based monitoring to flag anomalies such as unusual logins, privilege escalations, or excessive RDP activity.
- Application & Driver Control - Enforce application whitelisting to block unauthorized executables in user and temporary directories. Mitigate Bring Your Own Vulnerable Driver (BYOVD) attacks with solutions like Microsoft Defender Application Control.
- Access & Privilege Restrictions - Apply least-privilege principles to minimize admin or SYSTEM-level rights. Closely monitor for token manipulation, impersonation, and suspicious service creations.
- Data Protection & Loss Prevention - Use DLP solutions to detect and restrict unauthorized data transfers via SFTP, WebDAV, or cloud platforms. Implement outbound traffic filtering to block malicious IPs, Tor nodes, and ransomware leak sites.
- Robust Backup & Recovery Readiness - Maintain offline, immutable backups stored separately from the main network. Regularly test restoration processes to ensure business continuity after an attack.
- Log & Registry Monitoring - Forward system and security logs to a centralized SIEM for retention and review. Monitor for sudden log clearing, unusual registry modifications, or unauthorized scheduled task creations.
- Incident Response & Preparedness - Develop and test incident response playbooks covering detection, containment, recovery, and communication during ransomware incidents. Run tabletop exercises simulating DragonForce-style double extortion attacks.
- Threat Intelligence Integration - Continuously track Indicators of Compromise (IoCs), tactics, and affiliate behaviors linked to DragonForce through trusted intelligence feeds to stay ahead of evolving threats.
Why use LOVI to track ransomware like DragonForce?
LOVI is a real-time vulnerability intelligence platform that helps organizations identify, analyze, and respond to emerging threats faster. It consolidates data from vulnerability feeds, exploit sources, and dark web channels to deliver detailed insights into vulnerabilities, threat actors, and active ransomware operations.
By tracking Indicators of Compromise (IoCs), TTPs, and exploit trends, LOVI provides actionable intelligence that strengthens proactive defense. When monitoring ransomware like DragonForce, LOVI offers visibility into leak sites, affiliate networks, and exploited vulnerabilities, helping organizations anticipate attacks, prioritize patches, and stay ahead of evolving ransomware campaigns.
FAQs
1. What is Ransomware-as-a-Service (RaaS) and how does it work?
RaaS is a model where ransomware developers lease their malware to affiliates, who conduct attacks and share a portion of the ransom revenue with the developers, enabling wider reach and scalability.
2. How does DragonForce spread across networks?
It spreads via phishing emails, malicious documents, fake login portals, and exploitation of software vulnerabilities, often leveraging stolen credentials and social engineering.
3. Why are healthcare, finance, and education sectors common ransomware targets?
These sectors hold sensitive data, critical operations, and are more likely to pay ransoms, making them attractive targets for financially motivated threat actors.
Get Notified
BLOGS AND RESOURCES








