Introduction
As AI systems become more integrated into enterprise ecosystems, the need for standardized and secure communication between Large Language Models (LLMs) and external systems has never been greater. Enter the Model Context Protocol (MCP) - an open standard that bridges the gap between AI models, data sources, and tools.
MCP enables AI-to-system connectivity through a consistent, secure, and extensible protocol that allows LLMs to access external databases, APIs, and files seamlessly. But as with any powerful integration layer, understanding security best practices is critical to prevent data leakage, unauthorized access, and compliance failures - especially in cloud environments like Azure.
Key Takeaways
- MCP standardizes AI integration
- Security-first deployment is essential - especially in Azure environments.
- Zero Trust and continuous monitoring ensure long-term resilience.
What is Model Context Protocol (MCP)?
The Model Context Protocol (MCP) represents a sophisticated approach to connecting AI systems with the broader digital ecosystem. This open standard innovation creates seamless pathways between Large Language Models (LLMs) and the wide range of external resources they need to access, including databases, File systems, APIs, and specialised tools.
Why MCP Matters to Addressing a Critical Gap in AI Infrastructure to Addressing a Critical Gap in AI Infrastructure
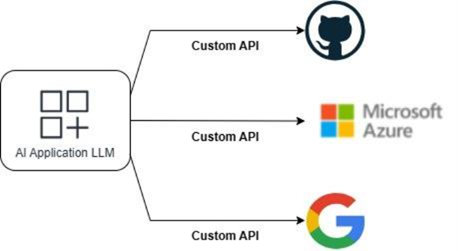
Before MCP's introduction, the AI development landscape was plagued by a significant challenge: the lack of standardised communication between AI models and external systems. This fragmentation forced developers to create bespoke integration solutions for each unique connection, resulting in:
- Development Overhead: Teams spent countless hours building custom connectors rather than focusing on core AI functionality.
- Maintenance Burden: Each integration required ongoing updates and maintenance as systems evolved.
- Reliability Issues: Ad-hoc connections often broke down, leading to inconsistent AI performance.
- Security Vulnerabilities: Custom implementations frequently lacked proper security protocols.
The MCP Solution
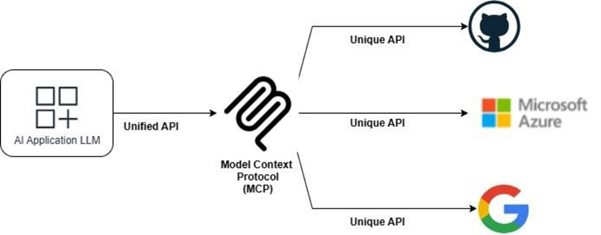
By establishing a universal protocol for AI-to-system communication, MCP eliminates the need for repetitive custom development work. Instead of building individual bridges between every AI application and external service, developers can now implement a single, standardised interface that works across multiple platforms and data sources.
This standardisation brings several key advantages:
- Accelerated Development: Teams can integrate new data sources quickly using existing MCP implementations.
- Enhanced Reliability: Standardised connections reduce the likelihood of integration failures.
- Improved Security: Built-in security protocols ensure safer data exchanges.
- Ecosystem Growth: A common standard encourages broader adoption and community contributions.
- Enables Smarter, More Capable AI Agents: Instead of static chatbots, MCP-backed agents can fetch current events, run code, update user accounts, and interact robustly with business data.
- Streamlines Security and Governance: Centralised context and permission management mean safer AI deployments within enterprises and regulated environments.
MCP Architecture
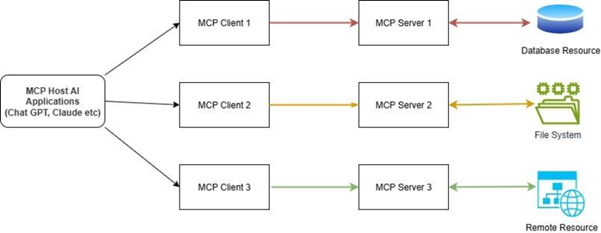
MCP Architecture is composed of four key components:
- MCP Host: The primary AI application (such as LLM-enabled IDEs or chatbots) responsible for client management and connection oversight, user authorisation handling, and context consolidation across multiple integrations.
- MCP Client: Integrated within the Host, every client establishes an exclusive, stateful link with one MCP server. Clients handle message routing, protocol version negotiation, capability management, and resource subscription services.
- MCP Server: Specialised processes (either local or remote) that provide tools, data, resources, and prompts to clients. Every server concentrates on a particular integration target, like a database or enterprise application.
- Protocol: MCP employs JSON-RPC 2.0 for communication, facilitating structured requests, responses, and notifications. Data exchange occurs through STDIO (local) or HTTP+SSE (remote) transport mechanisms for reliable, real-time communication.
Key Component Functions
Core Security Considerations
As we've covered through the technical foundations of MCP, understanding its powerful capabilities, architectural design, and the integration challenges it resolves, it's time to shift our focus to an equally important dimension: security.
For organisations considering MCP adoption, especially those planning deployments in Azure Cloud environments, understanding these security implications isn't just recommended, it's essential.
In the following sections, we'll examine the key security considerations that should guide your MCP deployment strategy, helping you leverage its capabilities while maintaining strong security in your cloud infrastructure.
Authentication & Authorisation
- MCP’s default configuration may lack strong authentication, exposing risks such as rogue server introduction, connection hijacking, and credential theft.
- Integrate Azure Entra ID for centralised identity management.
- Enforce multi-factor authentication (MFA), conditional access, and token-based authentication for all MCP endpoints.
Least Privilege & Access Control
- MCP tools are highly privileged by design.
- Always operate on a least privilege principle.
- Apply Azure Role-Based Access Control (RBAC) to ensure only authorised users, agents, and service principals can invoke MCP tools.
User Consent & Data Privacy
- MCP allows external servers to request or act on sensitive enterprise data.
- Require explicit user consent prior to data sharing.
- Apply data classification, masking, and access reviews before granting tool access.
Tool Safety & Code Execution
- Third-party tool integrations can introduce arbitrary code execution risks.
- Treat all external MCP tools as untrusted until verified.
- Require manual approval for tools that interact with external resources or execute system-level operations.
Monitoring, Logging & Incident Response
- Implement continuous monitoring with Microsoft Defender for Cloud, Microsoft Sentinel (SIEM), and Log Analytics.
- Enable logging for all MCP interactions, data access, and tool executions.
- Standardise retention for forensic analysis and compliance requirements.
Input/Output Validation & Network Controls
- Rigorously validate all data exchanged through MCP to prevent injection, corruption, or exfiltration.
- Use Azure Firewall, Private Endpoints, and NSGs to limit MCP exposure and control data flows.
Zero Trust & Defence-in-Depth
- Apply Zero Trust principles: authenticate, authorize, and inspect every MCP request.
- Enforce layered protections across identity, network, host, and data.
Governance & Operational Practices
- Establish documented governance for MCP implementations:
- Tool vetting process
- Incident handling procedures
- Periodic security reviews
- Integrate MCP-specific security into broader Azure AI governance frameworks.
Azure-Specific Integration Considerations
- Use official Azure MCP Server templates where possible for built-in security features.
- Harden integrations with services such as Azure Data Explorer by restricting external access and performing regular vulnerability reviews.
Continuous Updates & Community Practices
- MCP is open source and evolving rapidly.
- Apply security patches promptly.
- Track official documentation and participate in enterprise security forums to remain aligned with emerging best practices.
Azure Deployment Options for MCP Servers
Azure provides multiple deployment options for MCP servers, each suited to different requirements and use cases. The choice depends on factors such as control requirements, scalability needs, security considerations, and operational preferences.
Below is a comprehensive overview of the available options:
Network Security for MCP Traffic in Azure
Securing MCP traffic requires a comprehensive network security strategy that protects data in transit and prevents unauthorized access. Azure provides multiple network security tools and services that can be layered together to create a robust defence-in-depth approach for MCP deployments.
The following security measures should be implemented to ensure safe and secure MCP communications:
Additional Azure Services requiring access controls for MCP
Certain Azure services expose sensitive operations via MCP and demand stronger access controls.
Key Services & Controls
- Azure Key Vault – Limit access to secrets, keys, and certificates via RBAC and managed identities. Avoid credential leakage by enforcing tool-level approvals.
- Azure Cosmos DB & Databases – Restrict query/management operations to granular permissions. Enable database audit logging.
- Azure Storage (Blob, Table, Queue) – Use scoped SAS tokens, role-based permissions, and session approvals for MCP-enabled file/data access.
- Azure AI Services – Limit agent access to only required endpoints. Isolate sensitive or regulated data environments.
- Azure API Management – Configure custom access policies (rate limiting, IP restrictions, JWT/Managed Identity authentication).
- Azure Logic Apps & Integration Services – Secure automated workflows with explicit identity scoping, consent approvals, and Zero Trust policies.
- Azure Data Explorer (ADX/Kusto) – Restrict to read-only/query access unless write access is strictly justified. Enable monitoring for suspicious queries.
Moving Forward Securely
Azure provides robust tools for secure MCP deployment, including Azure Entra ID for identity management, Defender for Cloud, Policies, Private Endpoints, Firewalls, NSG for network isolation, and comprehensive monitoring etc. The key is implementing these security measures from day one rather than retrofitting them later.
Equally important is recognising that MCP is rapidly evolving. As an open standard under active development, new capabilities and security considerations emerge regularly. Organisations must maintain vigilance, stay connected with the development community, and continuously update their security postures to match the protocol's evolution.
FAQs - on Model Context Protocol (MCP)
What is the Model Context Protocol (MCP) used for?
MCP is an open standard protocol primarily developed by Anthropic (Claude) in November 2024enables AI models to interact with external systems like APIs, databases, and files securely and efficiently.
Why is MCP important for AI developers?
It eliminates the need for custom integrations, improving speed, scalability, and security in AI-powered solutions.
How can organizations secure MCP in Azure?
By enforcing Azure Entra ID authentication, using RBAC, applying network isolation (via NSGs and Private Endpoints), and adopting Zero Trust policies.
Does MCP support Zero Trust Architecture?
Yes - MCP aligns well with Zero Trust principles, ensuring that every access request is authenticated, authorized, and continuously verified.
Get Notified
BLOGS AND RESOURCES








