Improper access control in D-link Firmware DIR-601
Loginsoft-2020-1009
31 March, 2020
CVE Number
CWE
CWE-284: Improper Access Control
Product Details
D-Link introduces the Wireless N 150 Home Router (DIR-601), which delivers high performance end-to-end wireless connectivity based on Wireless N technology. The DIR-601 provides better wireless coverage and improved speeds over previous-generation Wireless G*. Upgrading your home network to Wireless N 150 provides an excellent solution for experiencing better wireless performance while sharing a broadband Internet connection with multiple computers over a secure wireless network.
URL: Wireless router
Vulnerable Firmware Versions
2.02NA
Hardware
B1
Vulnerability Details
The software does not restrict or incorrectly restricts access to a resource from an unauthorized actor
Analysis
Steps to reproduce:Method 1
- Log in as a user & visit http://192.168.0.1/tools_admin.htm .
- Right-click on the admin “password” input field and click on the inspect element.
- Modify the input field, by removing the “disable” attribute, repeating the same for the “verify password” input field & “save settings” button.
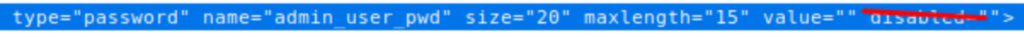
- Now enter new values to the available input field and click on submit. Now the password will be updated with supplied values.
Method 2
- Login as admin & visit http://192.168.0.1/tools_admin.htm .
- Intercept & record the request to change the admin password.
- Now login as a user & replay the recorded request, the admin’s password will be updated.
Exploitation
As part of the exploitation, the attacker (user account) can change the admin’s “password”, and similarly other settings, configurations available.
Mitigation
- Proper access control check needs to be employed, before processing the request.
Vendor Disclosure:
Credit
Discovered by ACE Team - Loginsoft







