Introduction
Cybersecurity in the Aviation Industry explores how increasing digitalization has made the aviation industry a high-value target for cyber threats. From flight operations and air traffic management to passenger data and airport infrastructure, expanding attack surfaces has led to a rise in cyber-attacks on aviation industry systems. The article highlights the evolving risk landscape, common attack vectors, and why strengthening Cybersecurity in Aviation is critical to ensuring safety, reliability, and operational continuity.
Key Takeaways
- Cybersecurity in Aviation Industry is critical due to highly interconnected digital systems.
- Attacks on aviation industry target operations and data with high-impact consequences.
- Cyber-attacks in the aviation industry can disrupt safety and continuity, not just IT systems.
- Proactive cybersecurity controls are essential to protect aviation infrastructure.
As the aviation sector advances toward complete digitalization, the benefits of streamlined operations, enhanced connectivity, and data-driven decision making are undeniable. However, this evolution significantly increases the industry's exposure to cyber threats. From air traffic control and onboard navigation to passenger data management and payment processing, every connected system presents a potential entry point for malicious actors. The stakes are high: given aviation's role in global transportation, commerce, and national security, a successful cyberattack could lead to operational disruptions, financial and reputational damage, and even risks to human safety.
Reflecting these growing threats, the aviation cybersecurity market is projected to be valued at approximately $5 billion to $10 billion in 2025, highlighting the increasing demand for protective solutions across the industry. Cybersecurity researchers have also noted a dramatic rise in attacks targeting aviation, including a 600% increase in ransomware incidents between 2024 and 2025, underscoring the urgent need for robust, industry-specific security measures. As the sector becomes ever more connected, safeguarding its complex and interdependent systems has shifted from being a strategic priority to a critical necessity for ensuring the resilience of global aviation infrastructure.
Why Cybercriminals target the aviation industry
The aviation industry has become one of the most attractive targets for cyber criminals, largely due to its scale, complexity, and the critical role it plays in global infrastructure. Several factors make airlines and their digital ecosystems particularly vulnerable:
1. Operational complexity
Airlines operations are among the most complex in the world, involving strict regulatory compliance, real-time logistics, and reliance on interconnected IT and OT systems. From ticketing and baggage handling to flight control and maintenance, each function is deeply interdependent. Disruptions in even a single component can cascade into large-scale operational failures, leading to flight delays, cancellations, and massive financial losses making these systems prime targets for attackers.
2. High Value of Passenger Data
Airlines collect vast amounts of sensitive data, including personal information, payment details, travel histories, and behavioral insights. This data is a goldmine for cybercriminals, who can resell it on underground markets, use it for identity theft, or leverage it in sophisticated phishing and social engineering campaigns.
3. Operational Disruption as leverage
Unlike many industries, aviation has very low tolerance for downtime. Cybercriminals exploit this by deploying ransomware or launching denial-of-service attacks, knowing that airlines may be willing to pay large ransoms to quickly restore services and avoid reputational damage. Even a short disruption can cost millions, making airlines highly motivated targets.
4. Geopolitical motivations
State-sponsored groups often target airlines to collect intelligence, monitor travel patterns, or disrupt critical national infrastructure. Such attacks may not be financially motivated but instead tied to espionage, political leverage, or destabilization efforts.
5. Exploiting passenger trust
Airlines are trusted by millions of passengers worldwide. A data breach or operational breakdown can severely undermine this trust, erode brand reputation, and provide attackers with significant bargaining power. The psychological impact of such incidents amplifies the damage well beyond the immediate technical compromise.
Types of attacks on aviation industry
- Ransomware
- Phishing
- Distributed Denial-of-Service (DDoS)
- Malware infiltration
- Data breaches
- Unauthorized network access
Recent Cyber attacks on aviation industry
Qantas Breach exposes millions of customer's records
In July 2025, Qantas, Australia's largest airline, disclosed a cyberattack that compromised customer information through a third-party servicing platform linked to its call center. The airline confirmed that while its core systems remain secure, the incident resulted in the theft of a significant amount of customer data. The exposed records are believed to affect up to 6 million customers and include names, email addresses, phone numbers, dates of birth, and frequent flyer numbers. Qantas emphasized that no credit card details, financial information, passwords, PINs, or login credentials were impacted. The airline has reported the breach to the Australian Cyber Security Centre, the Office of the Australian Information Commissioner, and the Australian Federal Police, while investigations into the scope of the incident are ongoing.
Hacktivists Claim Massive Cyberattack on Aeroflot
Another cyber incident in July 2025 targeted Russia's flag carrier Aeroflot that caused over 60 flight cancellations and widespread delays. While Moscow has not assigned blame, Ukrainian and Belarusian hacktivist groups Silent Crow and Cyberpartisans BY claimed responsibility, stating that they had infiltrated Aeroflot's IT infrastructure for over a year before wiping 7000 servers and exfiltrating more than 22 terabytes of sensitive data, including flight records, employee files, and call recordings. The hackers threatened to leak the stolen information, warning it would expose every Russian passenger. Although Aeroflot has not confirmed data loss, its ongoing disruptions point to significant IT damage. With a fleet of 171 aircraft and a 42% market share, the airline remains severely affected, with some flights operating without customer support.
Pro-Palestinian Hacktivists Launch DDoS Attack on Los Angeles International Airport
In March 2025, Los Angeles International Airport (LAX) was hit by a large-scale DDoS attack carried out by the pro-Palestinian hacktivist group "Dark Strom Team". The assault overwhelmed airport systems with fake traffic, disrupting flight information displays, baggage handling, and electronic check-in services. While no flights were cancelled, the incident caused significant delays and confusion, with blank screens, slowed websites and staff forced to manage passenger flows manually. Authorities confirmed the attack was politically motivated, with no data breach or ransom demands involved, linking it to the U.S. support for Israel. Security analysts reported the use of advanced botnets capable of bypassing standard defenses, noting that while services were restored once the attack subsided, LAX likely suffered financial and reputational setbacks. The incident underscored how even short-term hacktivist campaigns can severely impact critical aviation operations.
Ransomware Attack Disrupts Kuala Lumpur International Airport
In March 2025, Kuala Lumpur International Airport (KLIA) was hit by a significant ransomware attack that brought critical systems down for over 10 hours, forcing staff to revert to manual operations, including handwritten flight updates. The attackers, reportedly the Qilin Ransomware group, demanded a $10 million ransom and claimed to have exfiltrated 2 TB of data, though the Malaysian government confirmed it would not pay. The incident prompted an immediate response from the nation's cyber agency, which initiated the recovery efforts the same day. While no official attribution was provided, the attack is considered one of the most disruptive cyber incidents to affect an Asian airport, highlighting vulnerabilities in aviation cybersecurity and underscoring the need for stronger segmentation, phishing prevention, and routine security testing.
Strengthening Cybersecurity in Aviation:
The airline industry faces increasingly sophisticated cyber threats, underscoring the urgent need for a comprehensive and resilient cybersecurity framework tailored specifically for air transportation. While existing standards like ISO/IEC 27001:2013 provide foundational security guidelines, they fall short in addressing critical aspects such as incident response during in-flight cyberattacks.
Key international bodies including the International Civil Aviation Organization (ICAO), National Cyber Security Centre (NCSC), European Union Aviation Safety Agency (EASA), Airport Council International (ACI) World, International Air Transport Association (IATA), and the European Organization for the Safety of Air Navigation (Eurocontrol), have partnered with the World Economic Forum (WEF) to establish a baseline of best cybersecurity practices for the aviation sector. This collaborative effort aims to elevate industry-wide security standards, acknowledging the unique challenges faced by air transport. Developing a robust cybersecurity framework demands a holistic approach that encompasses the entire aviation ecosystem: airlines, airports, aircraft manufacturers, satellite communication providers, air navigation service providers, and telecommunication companies. Each stakeholder plays a vital role in safeguarding the digital infrastructure and must collaborate to establish prevention, detection, and rapid response mechanisms to emerging cyber threats.
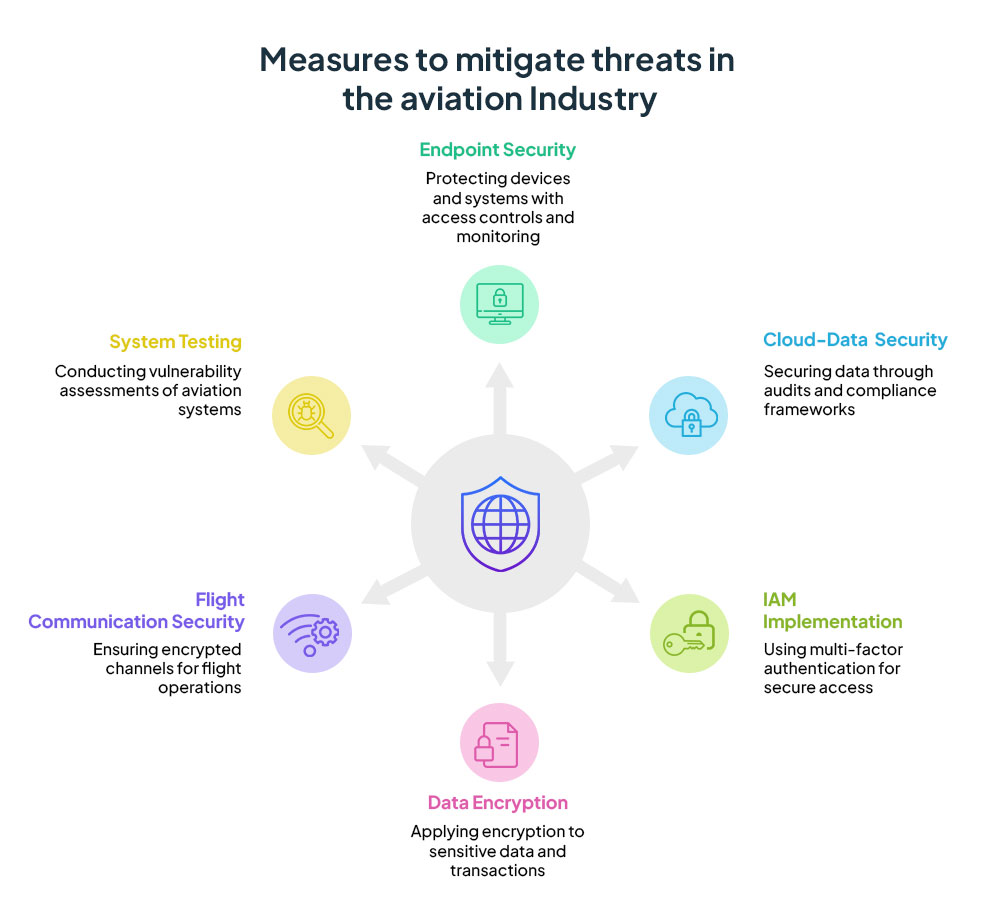
The Takeaway: Safeguarding Aviation’s Communication Touchpoints
Traditionally, airlines have concentrated much of their cybersecurity efforts on preventing data breaches. However, the more pressing challenge lies in securing the transmission of data across multiple vulnerable touchpoints. These include communications between ground control and aircraft during flights, interactions within airport environments, and data exchanges between onboard sensors and communication devices. Given the critical nature of these channels, any compromise could jeopardize flight safety and operational integrity.
As cyber risks continue to evolve, the aviation industry must prioritize proactive threat monitoring and incident response planning, particularly for scenarios involving in-flight cyber incidents. While a unified industry-wide initiative is still in development, the urgency to enhance cyber resilience across all components of the air transportation network is clear. Ultimately, preparedness and cross-sector cooperation will be key to ensuring the safety and security of air travel in the digital age.
Conclusion
The blog highlights that Cybersecurity in Aviation is no longer optional but a core requirement for maintaining trust, safety, and resilience. As cyber-attacks on aviation industry systems grow in sophistication, organizations must prioritize visibility, risk management, and defense strategies across both IT and operational environments. Strengthening Cybersecurity in the Aviation Industry is essential to safeguarding critical systems, protecting passenger data, and ensuring uninterrupted aviation operations.
FAQs
Q1. Why is Cybersecurity in the Aviation Industry important?
Because aviation relies on complex digital systems where cyber incidents can directly impact safety and operations.
Q2. What types of attacks affect the aviation industry?
Attacks include data breaches, system disruptions, ransomware, and attacks on operational technology.
Q3. Why are cyber-attacks on aviation industry systems high risk?
Because disruptions can affect flight operations, passenger safety, and critical infrastructure.
Q4. What areas are most vulnerable in aviation cybersecurity?
Air traffic systems, airport operations, airline IT systems, and passenger data platforms.
Q5. What is the key takeaway for improving Cybersecurity in Aviation?
Organizations must adopt proactive, layered security strategies to reduce risk and ensure operational resilience.
Get Notified
BLOGS AND RESOURCES








