Introduction
Ghost Ransomware Playbook: How It Works, What It Uses, and How to Prevent It, provides a detailed breakdown of Ghost Ransomware, outlining its operational flow, tooling, and attack techniques. The article explains how Ghost ransomware campaigns are executed, from initial access to encryption, and highlights overlaps with Cring Ransomware, indicating shared behaviors and tactics. By presenting a structured Ghost Ransomware Playbook, the blog helps defenders understand how these attacks unfold and how they can be prevented.
Key Takeaways
- Ghost Ransomware follows a defined playbook from access to encryption.
- Attack techniques overlap with Cring Ransomware, indicating shared tactics.
- Attackers rely on common tools and misconfigurations to gain control.
- Early detection disrupts the ransomware playbook before encryption occurs.
Emerging as a silent predator in the cyber threat landscape, Ghost (aka Cring) ransomware resurfaced in early 2025 with intensified tactics, exploiting vulnerable systems worldwide and leaving a trail of encrypted chaos across over 70 countries.
Originally identified in 2021, Ghost is a financially motivated threat group believed to have originated in China, though its attacks are indiscriminate and global in reach, including domestic targets. The group is known for exploiting unpatched, public-facing services to gain access and disrupt operations, particularly in sectors with high uptime requirements.
What makes Ghost particularly elusive is its ability to constantly evolve, frequently rotating ransomware payloads, ransom notes, and even file extensions. This operational fluidity has led researchers to link it with other aliases including Cring, Crypt3r, Phantom, Strike, Hello, Wickrme, HsHarada, and Rapture. Ransomware samples observed in the wild include Cring.exe, Ghost.exe, ElysiumO.exe, and Locker.exe, further complicating identification and reinforcing the group's evasive nature. Leveraging advanced obfuscation and anti-analysis techniques, Ghost remains a persistent and adaptive threat in today's rapidly evolving ransomware ecosystem.
Targeted Industries: Finance, Transportation, Healthcare, Education, Government, Technology, Manufacturing
Targeted Countries: Azerbaijan, Brazil, Italy, Mexico, Saudi Arabia, United States, Turkey, Canada, United Kingdom, Germany, France, India, China and Japan.
Technical Analysis
Initial Access
Ghost threat actors often achieve initial access by exploiting critical, unpatched vulnerabilities in internet-facing systems. By targeting widely used technologies, they are able to infiltrate networks quickly and with minimal resistance, frequently compromising environments before defenders can react.
Ghost actors are known to gain initial foothold into targeted networks by exploiting vulnerabilities in internet-facing applications. Their attack strategy often involves targeting unpatched systems, particularly Fortinet FortiOS appliances, as well as servers running Adobe ColdFusion, Microsoft SharePoint, and Microsoft Exchange. By taking advantage of these exposed and vulnerable platforms, they establish early-stage access for further compromise.
Vulnerabilities abused by Ghost Ransomware
Execution and Persistence
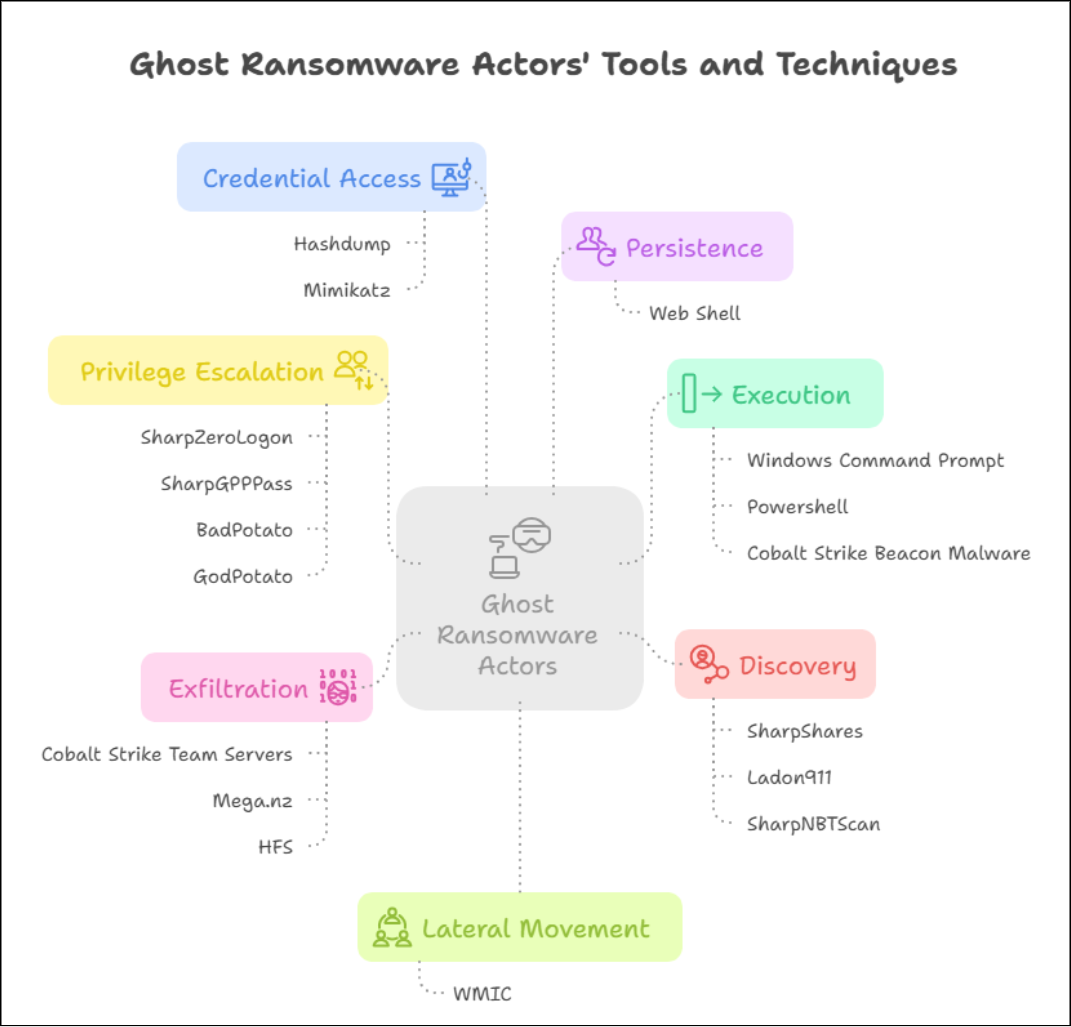
After gaining initial access, Ghost threat actors quickly escalate their operations by deploying web shells and utilizing tools like PowerShell or Command Prompt to execute Cobalt Strike Beacon for remote control. Although they may occasionally create or modify local and domain accounts to maintain short-term access, persistence is not their primary objective. Their attacks are characterized by speed and aggression, often progressing from compromise to ransomware deployment within hours, making rapid detection and response critical.
Privilege Escalation
For privilege escalation, Ghost threat actors frequently abuse built-in Cobalt Strike capabilities to steal process tokens associated with the SYSTEM user context. This allows them to impersonate the SYSTEM account and, in many cases, re-execute the Beacon payload with elevated privileges. In addition to these built-in functions, Ghost operators have also been observed leveraging various open-source tools to escalate privileges by exploiting known vulnerabilities. Notable tools in their arsenal include SharpZeroLogon, SharpGPPPass, BadPotato, and GodPotato, each designed to exploit Windows privilege escalation flaws.
Defense Evasion
As part of their defense evasion tactics, Ghost threat actors leverage their Cobalt Strike access to enumerate running processes and identify active antivirus or endpoint protection tools. Once detected, they take steps to disable these defenses to avoid detection and ensure the success of their payloads. A common tactic includes executing PowerShell commands to disable Windows Defender on network-connected devices. Specifically, they use the Set-MpPreference command with multiple flags to turn off real-time monitoring, intrusion prevention, behavior monitoring, script scanning, and other key protective features.
Additionally, they disable controlled folder access and reporting functionalities to further reduce visibility and prevent threat intelligence sharing. This systematic deactivation of security controls enables Ghost actors to operate stealthily within compromised environments.
Credential Access
Ghost threat actors achieve credential access by using Cobalt Strike's "hashdump" function or tools like Mimikatz to extract plaintext passwords and password hashes from memory. These harvested credentials allow them to impersonate legitimate users, escalate privileges, and move laterally across the network, significantly expanding their reach within the compromised environment.
Discovery
As part of their discovery tactics, Ghost actors leveraged built-in Cobalt Strike commands and offensive security tools to map out target environments. For domain account enumeration, they utilize native Cobalt Strike functionalities, while tools like SharpShares are deployed to identify accessible network shares. Additionally, Ladon 911 and SharpNBTScan are used for scanning and enumerating remote systems. These tools, typically associated with adversarial use, are not commonly employed by legitimate network administrators for routine discovery tasks, highlighting their role in malicious reconnaissance activities.
Lateral Movement
During the lateral movement phase, Ghost actors leverage previously escalated privileges and use Windows Management Instrumentation Command-Line (WMIC) to execute Base64-encoded PowerShell commands across victim networks. These commands deploy additional Cobalt Strike Beacon payloads on remote systems, with the encoded strings typically beginning with:
powershell -nop -w hidden -encodedcommand
JABzAD0ATgBlAHcALQBPAGIAagBlAGMAdAAgAEkATwAuAE0AZQBtAG8AcgB5AFMAdAByAGUAYQBtACgALABbAEMAbwBuAHYAZQByAHQAXQA6ADoARgByAG8AbQBCAGEAcwBlADYANABTAHQAcgBpAG4AZwAoACIA…
When lateral movement fails, the actors often abandon the intrusion, indicating a strategic retreat upon encountering defensive friction.
Command and Control
Ghost actors heavily depend on Cobalt Strike Beacon and Team Servers to maintain command and control (C2) across compromised environments, utilizing HTTP and HTTPS protocols for communication. Rather than using registered domains for C2 infrastructure, they often opt for direct IP-based connections to access Beacon payloads via specific URIs, making detection and attribution more challenging.
For victim correspondence, Ghost actors rely on encrypted, privacy-focused email services such as Tutanota, Skiff, ProtonMail, Onionmail, and Mailfence, leveraging their secure communication channels to evade monitoring and maintain operational secrecy.
Exfiltration
Ghost actors utilize cloud storage platforms like mega.nz to exfiltrate sensitive victim data as part of their double extortion strategy, stealing data before encryption to increase leverage during ransom negotiations. By transferring confidential files to these external repositories, adversaries ensure they retain a copy of the victim's data, threatening to leak or sell it if ransom demands are not met.
Impact
On the impact side, Ghost actors deploy ransomware variants such as Cring.exe, Ghost.exe, ElysiumO.exe, and Locker.exe, all of which exhibit similar capabilities. These payloads can encrypt targeted directories or entire system drives, depending on the command-line arguments used at execution. To maintain system usability and ensure successful ransom communication, critical system folders and file types are often excluded from encryption.
Once deployed, the ransomware disables Volume Shadow Copy Service, deleted shadow copies, and clears Windows Event Logs to obstruct forensic recovery and inhibit restoration efforts. Encrypted data is rendered inaccessible without the attacker-provided decryption key, with ransom demands typically ranging from tens to hundreds of thousands of dollars in cryptocurrency.
MITRE ATT&CK Tactics and Techniques
Tools used by Ghost Ransomware
Indicators of Compromise:
The indicators below are associated with Ghost ransomware operations. Organizations should integrate these IoCs into their detection engines and threat hunting workflows for proactive defense.
Mitigation Strategies:
- Deploy EDR/XDR solutions to detect and block malicious activity in real-time.
- Segment networks and apply least privilege to limit lateral movement.
- Disable unnecessary services like SMBv1 and RDP to reduce attack surface.
- Monitor continuously for Ghost-related IoCs such as file hashes and ransom emails.
- Enforce multi-factor authentication (MFA) on all remote and admin accounts.
- Use strong, unique passwords and regularly update them.
- Apply patches for known vulnerabilities.
- Implement email filtering and block phishing attempts effectively.
- Maintain regular, offline encrypted backups and test data recovery processes.
- Develop and regularly update an incident response plan for ransomware attacks.
Conclusion
The blog highlights that Ghost Ransomware is not a random or opportunistic threat but a structured operation driven by a repeatable Ghost Ransomware Playbook. The similarities with Cring Ransomware reinforce how attackers reuse proven techniques to accelerate campaigns. Understanding this playbook enables organizations to detect early-stage activity, apply preventive controls, and significantly reduce the impact of ransomware attacks.
FAQs
Q1. What is Ghost Ransomware?
Ghost Ransomware is a ransomware threat that uses a structured attack process to compromise systems and encrypt data.
Q2. What is the Ghost Ransomware Playbook?
It refers to the documented sequence of tactics, tools, and techniques attackers use during Ghost ransomware attacks.
Q3. How is Ghost Ransomware related to Cring Ransomware?
They share similar behaviors and tactics, suggesting reused techniques or operational overlap.
Q4. How can organizations prevent Ghost Ransomware attacks?
By identifying early indicators, securing exposed systems, and monitoring attacker behavior before encryption.
Get Notified
BLOGS AND RESOURCES








