Introduction
TLS 1.3 - the newest version of Transport Layer Security (TLS) - represents a major upgrade in encryption, speed, and security. It’s faster, safer, and leaner than TLS 1.2, removing insecure ciphers and adding modern cryptography for privacy-first communications.
While TLS 1.3 is already default in major browsers and runtimes, its adoption across Azure cloud services remains inconsistent. This blog helps cloud architects, DevOps, and security engineers understand where Azure supports TLS 1.3, where enforcement is possible, and how to plan a phased rollout to maintain compliance and uptime.
Key Takeaways
- TLS 1.3 is now the industry benchmark for secure, low-latency cloud communication.
- Azure TLS 1.3 support varies - some services (App Service, Front Door) allow enforcement, while others (Storage, IoT Hub) still cap at TLS 1.2.
- Plan enforcement in phases - enforce client-facing workloads first, pilot for hybrid apps, and prepare legacy integrations.
What is TLS 1.3?
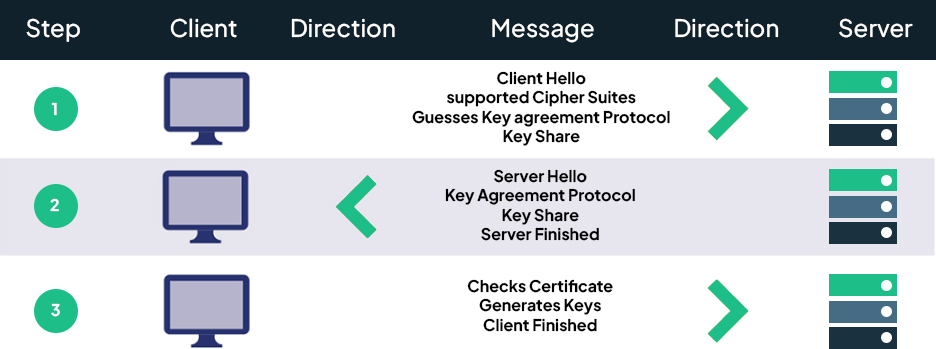
TLS 1.3 (Transport Layer Security 1.3) is a cryptographic protocol used to encrypt data in transit over the internet or within cloud networks. It’s the successor to TLS 1.2 and introduces major improvements designed for today’s cloud-native, API-driven environments.
Key Improvements in TLS 1.3
- Faster handshakes: Reduces latency by requiring just one round trip between client and server.
- Stronger encryption: Removes outdated algorithms like RSA key exchange and weak ciphers.
- Forward secrecy by default: Protects historical data even if long-term keys are compromised.
- Encrypted handshakes: Minimizes metadata exposure and protects certificate details.
In short, TLS 1.3 is the cornerstone of modern cloud security - ensuring high performance and confidentiality across services like Azure, AWS, and GCP.
Why TLS 1.3 Matters for Azure Security
For enterprises relying on Azure, TLS 1.3 adoption isn’t just about staying current - it’s about reducing attack surface and improving connection performance across distributed applications.
Benefits include:
- Lower Latency: Applications and APIs experience faster load and handshake times.
- Stronger Security: Legacy cryptographic suites are deprecated.
- Future-Ready Compliance: Frameworks like PCI DSS 4.0 and NIST SP 800-52r2 are making TLS 1.3 the new default by 2025–2030.
Learn more about Azure Security Hardening from Logisoft's experts.
The Azure Reality Check: Uneven TLS 1.3 Adoption
While most clients, browsers, and SDKs already support TLS 1.3, Azure’s service-level adoption is uneven:
- Some services fully support and enforce TLS 1.3 (App Service, Front Door, Event Hubs, etc.).
- Some support TLS 1.3 traffic but can’t enforce it yet (SQL, Cosmos DB, Redis).
- Others still limit enforcement to TLS 1.2 (IoT Hub, certain Storage SKUs).
This disparity makes it difficult for enterprises to set consistent encryption baselines or apply uniform Azure Policy enforcement for TLS governance.
How We Assessed Azure Services
Our evaluation focused on two key dimensions:
1. Functionality Risk
How likely is enforcement to cause service disruption?
- Low Risk: Modern workloads (App Service, Front Door, App Gateway).
- Medium Risk: Hybrid workloads using mixed SDKs or connectors (Event Hubs, Service Bus).
- High Risk: Legacy-heavy or IoT workloads (Storage, Cosmos DB, IoT Hub).
2. Policy & Enforcement Readiness
Can Azure Policy or configuration enforce TLS 1.3?
- Some services expose min Tls Version property for audit/enforcement.
- Others support TLS 1.3 implicitly but lack a configurable enforcement toggle.
This framework enables decision-makers to prioritize safe enforcement while maintaining availability.
Azure TLS 1.3 Support Snapshot (2025 Update)
How to Roll Out TLS 1.3 Safely Across Azure
- Inventory your clients: Identify apps and APIs still using TLS 1.2.
- Upgrade runtimes: Adopt modern SDKs (.NET 8+, Java 17+, Python 3.10+).
- Pilot gradually: Enable TLS 1.3 on low-risk endpoints (App Service, Front Door).
- Monitor TLS telemetry: Track negotiated versions using Azure Monitor or Defender for Cloud.
- Engage partners: Coordinate upgrade timelines with SaaS or vendor integrations.
- Enforce with policy: Use minTls Version where available; document gaps.
Pro Tip: Regularly review the Azure TLS 1.3 support roadmap to stay ahead of service-level updates.
Real-World Scenarios for TLS 1.3
- SaaS Acceleration:
A global SaaS company hosted APIs on Azure App Service and enforced TLS 1.3-only endpoints. Result: 15% lower latency and improved SEO page performance.
- Financial Data Integrity:
A banking client using Event Hubs upgraded its Kafka clients for TLS 1.3 compliance, reducing failed handshakes and audit findings.
- IoT Preparedness:
An industrial IoT firm upgraded its firmware stack for 25K devices before Microsoft enforced TLS 1.3 on Azure IoT Hub.
Challenges & Pitfalls for TLS 1.3 Implementation
Despite its advantages, TLS 1.3 adoption in Azure environments introduces technical and operational challenges:
1. Compatibility Issues with Legacy Systems
Older middleware, firewalls, and monitoring tools might not recognize TLS 1.3 handshakes or cipher suites, causing connection failures or degraded performance.
2. TLS Inspection and Visibility Loss
Network monitoring tools relying on session decryption (e.g., IDS/IPS) may lose visibility since TLS 1.3 encrypts more handshake details, impacting traffic analysis and DLP tools.
3. Load Balancer and CDN Layer Conflicts
Some hybrid Azure setups (Front Door + CDN + App Gateway) require consistent cipher and version settings to avoid SSL mismatch errors.
4. Testing and Rollout Complexity
Enterprises often underestimate the need for staged deployment testing - especially for APIs, client apps, and IoT endpoints that use strict TLS validation.
5. Configuration Drift in Multi-Region Deployments
Managing identical TLS configurations across regions is difficult, often leading to misconfigurations and security policy inconsistencies.
Best Practices for TLS 1.3 Adoption in Azure
To ensure a seamless rollout and optimal security posture, organizations should follow these implementation best practices:
1. Perform Compatibility Testing
- Validate all connected systems, APIs, and third-party integrations for TLS 1.3 handshake compatibility.
- Use tools like SSL Labs, Wireshark, or Microsoft Defender for Cloud Recommendations to audit support readiness.
2. Enforce Secure Cipher Suites
- Restrict weak ciphers and enforce AES-GCM or ChaCha20-Poly1305 encryption for all inbound/outbound traffic.
3. Implement Phased Rollouts
- Adopt TLS 1.3 gradually starting with Azure Front Door and App Gateway, before extending to internal applications.
4. Monitor Using Azure Policy and Logs
- Enable Azure Monitor, Application Insights, and Network Watcher to track handshake errors, performance metrics, and security alerts.
5. Update Security Tooling
- Ensure WAFs, load balancers, and SIEM integrations (like Sentinel or Splunk) can parse TLS 1.3 logs properly to maintain detection visibility.
6. Enable HTTP/3 Were Supported
- Combine TLS 1.3 with HTTP/3 (QUIC) to improve connection resilience and throughput for edge-delivered apps.
The Road Ahead: What’s Next for TLS 1.3 on Azure
Microsoft is steadily expanding TLS 1.3 enforcement across major services, with Storage, SQL, and Cosmos DB expected next.
Meanwhile, industry mandates (PCI DSS 4.0, ISO 27001 updates) continue to make TLS 1.3 the global encryption baseline.
Bottom Line:
TLS 1.3 is the future of secure cloud networking. Enforce it where supported, prepare where it’s not, and continuously monitor across all workloads.
Conclusion
The move toward TLS 1.3 Azure Support represents a strategic step forward for organizations aiming to modernize their Transport Layer Security in Cloud.
While Azure continues its gradual adoption, enterprises must take a planned, tested, and policy-driven approach to implementation - balancing security with compatibility.
By addressing common pitfalls and following best practices, teams can achieve better performance, compliance, and trust in their Azure Security Hardening journey.
Loginsoft POV: Building Secure Cloud Foundations
At Loginsoft, we help enterprises strengthen cloud security through advanced engineering, governance, and integration services.
Our experts support organizations by:
- Auditing TLS configurations across Azure and hybrid ecosystems.
- Designing Transport Layer Security (TLS) enforcement frameworks using Azure Policy and automation.
- Integrating telemetry and alerts with SIEM platforms and Threat Intelligence systems to detect downgrade attempts.
TLS 1.3 adoption is a journey - and with proactive preparation, your organization can be secure, compliant, and cloud-optimized.
Explore more on Cybersecurity Engineering Services.
FAQs: Azure TLS 1.3 Support
Q1. Does Azure support TLS 1.3?
Yes. Azure services like App Service, App Gateway v2, Front Door, and Logic Apps support TLS 1.3. Some services, like Storage or IoT Hub, currently only accept TLS 1.3 traffic but cannot enforce it yet.
Q2. How can I enable TLS 1.3 on Azure App Service?
Go to your App Service → TLS/SSL settings → select Minimum TLS version = 1.3 via the Azure Portal, ARM template, or CLI.
Q3. How do I audit TLS 1.3 enforcement across Azure?
Use Azure Policy to check the minTls Version field or run custom scripts with Azure CLI or PowerShell to verify configurations.
Q4. Is TLS 1.3 faster than TLS 1.2?
Yes. TLS 1.3 completes a secure handshake in one round trip instead of two, reducing latency and improving user experience.
Q5. Which Azure services are still limited to TLS 1.2?
SQL Database, some Storage Accounts, and IoT Hub currently cap enforcement at TLS 1.2, though updates are ongoing.
Get Notified
BLOGS AND RESOURCES









