Vulnerability Intelligence Annual Report 2025
Vulnerability Intelligence Annual Report 2025

A brute force attack uses trial-and-error to guess login in info, encryption keys, or find a hidden web page. Hackers work through all possible combinations hoping to guess correctly.
These attacks are done by ‘brute force’ meaning they use excessive forceful attempts to try and ‘force’ their way into your private account(s).
This is an old attack method, but it's still effective and popular with hackers. Because depending on the length and complexity of the password, cracking it can take anywhere from a few seconds to many years.
There are various types of brute force attack methods that allow attackers to gain unauthorized access and steal user data.
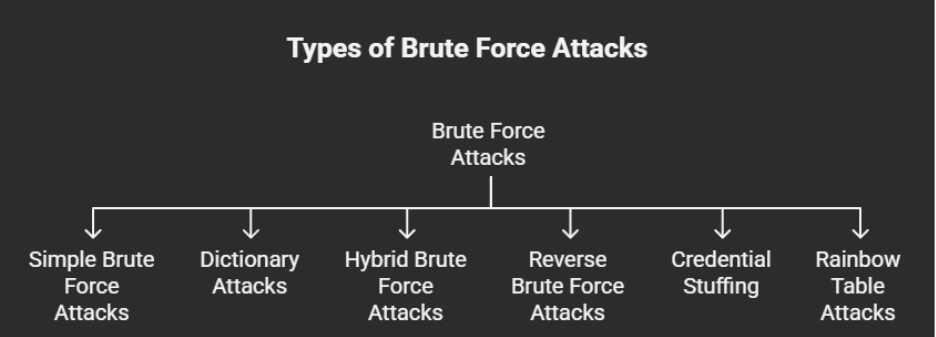
A simple brute force attack occurs when a hacker attempts to guess a user’s login credentials manually without using any software. This is typically through standard password combinations or personal identification number (PIN) codes.
These attacks are simple because many people still use weak passwords, such as "password123" or "1234," or practice poor password etiquette, such as using the same password for multiple websites. Passwords can also be guessed by hackers that do minimal reconnaissance work to crack an individual's potential password, such as the name of their favorite sports team.
A dictionary attack is a basic form of brute force hacking in which the attacker selects a target, then tests possible passwords against that individual’s username. The attack method itself is not technically considered a brute force attack, but it can play an important role in a bad actor’s password-cracking process.
The name "dictionary attack" comes from hackers running through dictionaries and amending words with special characters and numbers. This type of attack is typically time-consuming and has a low chance of success compared to newer, more effective attack methods.
A hybrid brute force attack is when a hacker combines a dictionary attack method with a simple brute force attack. It begins with the hacker knowing a username, then carrying out a dictionary attack and simple brute force methods to discover an account login combination.
The attacker starts with a list of potential words, then experiments with character, letter, and number combinations to find the correct password. This approach allows hackers to discover passwords that combine common or popular words with numbers, years, or random characters, such as "SanDiego123" or "Rover2020."
A reverse brute force attack sees an attacker begin the process with a known password, which is typically discovered through a network breach. They use that password to search for a matching login credential using lists of millions of usernames. Attackers may also use a commonly used weak password, such as "Password123," to search through a database of usernames for a match.
Credential stuffing preys on users’ weak password etiquettes. Attackers collect username and password combinations they have stolen, which they then test on other websites to see if they can gain access to additional user accounts. This approach is successful if people use the same username and password combination or reuse passwords for various accounts and social media profiles. These campaigns often escalate into identity-driven attack patterns that weaponize compromised accounts across multiple services.
A rainbow table attack is an offline password cracking technique that trades computing time for memory by using precomputed tables of hashes. Instead of hashing guessed passwords on the fly, attackers use a “rainbow table”, a giant lookup table of hash values for many possible passwords, to quickly match a hash to its original password.
The biggest advantage of brute force attacks is that they are relatively simple to perform and, given enough time and the lack of a mitigation strategy for the target, they always work. Every password-based system and encryption key out there can be cracked using a brute force attack. In fact, the amount of time it takes to brute force into a system is a useful metric for gauging at that system’s level of security.
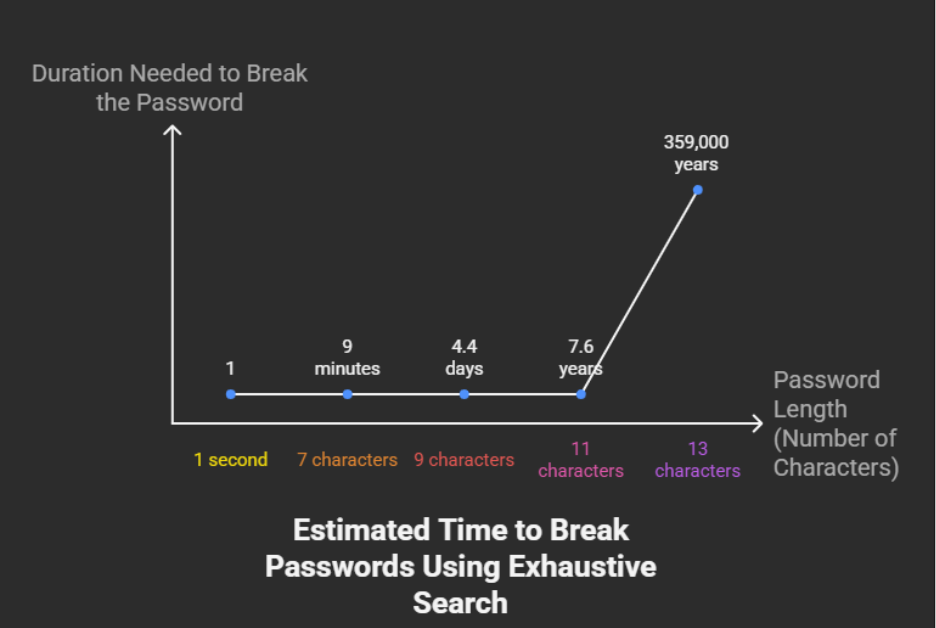
On the other hand, brute force attacks are very slow, as they may have to run through every possible combination of characters before achieving their goal. This sluggishness is compounded as the number of characters in the target string increases (a string is just a combination of characters). For example, a four-character password takes significantly longer to brute force than a three-character password, and a five-character password takes significantly longer than a four-character password. Once character count is beyond a certain point, brute forcing a properly randomized password becomes unrealistic.
If the target string is sufficiently long, then it could take a brute force attacker days, months, or even years to decode a properly randomized password. As a result of the current trend of requiring longer passwords and encryption keys, brute force attacks are quite a bit more difficult. When good passwords and encryption are utilized, attackers typically try other methods of code breaking such as social engineering or on-path attacks.
Here is the step-by-step process of how a brute force attack is done by attackers:
.png)
Once cracked, the attacker logs in or decrypts the file.
At Loginsoft, we understand how critical account security is to protecting users and enterprise systems. Our Security Engineering and Threat Intelligence Services help detect and respond to authentication-based attacks in real time.
We help organizations monitor login activity, enforce modern authentication controls, and correlate attempted attacks with active threat indicators. With continuous intelligence and automated defenses, Loginsoft helps reduce the success rate of brute force attacks and prevents account compromise before it leads to a larger breach.
Q1. What is a Brute Force Attack?
A brute force attack is a trial-and-error method where attackers try multiple passwords or keys until the correct one is found.
Q2. What makes brute force attacks effective?
Weak or reused passwords and lack of authentication controls make these attacks easier to execute successfully.
Q3. What is the difference between brute force and credential stuffing?
Credential stuffing uses known leaked passwords, while brute force attempts to guess new password combinations.
Q4. How long does a brute force attack take?
The time depends on password strength and security controls. Strong passwords and MFA can make brute force attacks nearly impossible.
Q5. How does Loginsoft help protect against brute force attacks?
Loginsoft offers monitoring, threat intelligence, and secure engineering support to strengthen authentication systems and stop automated attacks.