Vulnerability Intelligence Annual Report 2025
Vulnerability Intelligence Annual Report 2025

What Is Data Breach
A data breach is the release of confidential, private, or otherwise sensitive information into an unsecured environment. A data breach can occur accidentally, or as the result of a deliberate attack.
Millions of people are affected by data breaches every year, and they can range in scope from a doctor accidentally looking at the wrong patient’s chart, to a large-scale attempt to access government computers to uncover sensitive information.
A data breach can be caused by an outside attacker, who targets an organization or several organizations for specific types of data, or by people within an organization. Hackers select specific individuals with targeted cyberattacks.
Data breaches can be the result of a deliberate attack, an unintentional error or oversight by an employee, or flaws and vulnerabilities in an organization’s infrastructure.
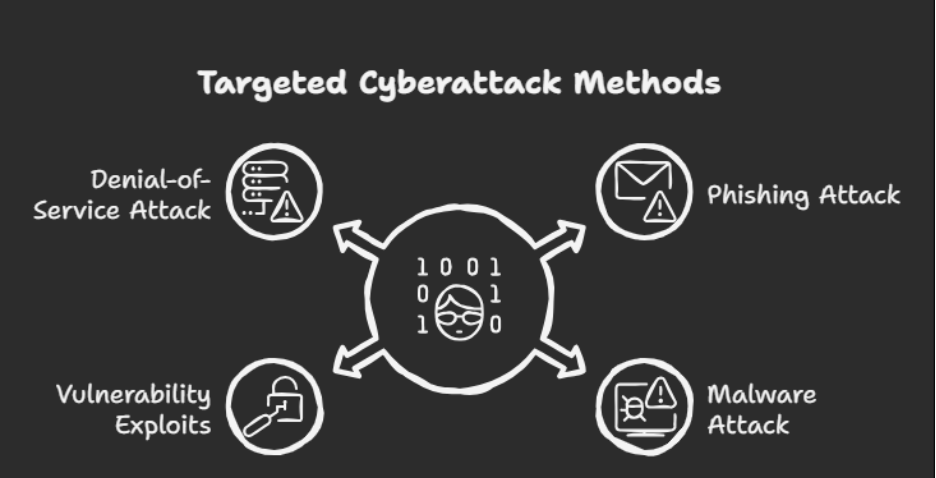
Financial motivation is the primary driver behind most data breaches. While no organization or individual is immune, certain industries are targeted more frequently due to the type and volume of data they manage. These often include government, healthcare, education, energy, and commercial enterprises.
Organizations with weak security controls are especially vulnerable. Common risk factors include unpatched systems, poor password hygiene, employees susceptible to phishing, compromised credentials, and lack of email or data encryption.
Attackers most often seek the following types of data:
Early detection and rapid response are crucial to limiting the damage caused by a data breach. Delays can significantly increase financial, legal, and reputational harm. A structured incident response process helps organizations act quickly and decisively.
The response typically involves the following seven phases:
1. Identify the Breach
Initial indicators may include vulnerability alerts, abnormal network behavior, suspicious login attempts, phishing emails, or external breach notifications. Breaches can also originate internally, such as when departing employees steal data.
2. Take Immediate Action
Record the exact time and date of discovery. Notify internal security and leadership teams, and immediately restrict access to affected systems or data.
3. Preserve Evidence
Interview those who discovered the incident, review security logs and monitoring tools, and track data movement across applications, servers, devices, and cloud services.
4. Analyze the Incident
Determine how the breach occurred by examining traffic patterns, access logs, affected systems, duration of exposure, and the data involved.
5. Contain, Secure, and Recover
Limit further access to compromised resources, protect evidence from alteration or deletion, and begin restoring affected systems to a secure state.
6. Notify Required Parties
Inform relevant stakeholders, regulatory bodies, and law enforcement as required by law and organizational policy.
7. Strengthen Future Defenses
Review the incident to identify gaps in security controls and implement improvements to prevent similar breaches in the future.
Security professionals widely recommend a defense-in-depth approach to reduce the risk and impact of data breaches. This strategy relies on multiple, overlapping security controls so that if one layer fails, others remain in place to protect sensitive data.
A strong multi-layered security framework typically includes:
From the perspective of a security services firm, a data breach must be treated as a risk scenario, not just a possibility. Key principles:
At Loginsoft, we treat “data breach prevention & response” as a core pillar of our security services, helping clients reduce exposure, detect early, and respond fast when incidents happen.
Q1. What is a data breach
A data breach is an incident where sensitive or confidential information is accessed or exposed without authorization.
Q2. What causes data breaches
Breaches can result from hacking, phishing, insider misuse, misconfigured systems, unpatched vulnerabilities, or accidental exposure.
Q3. What happens after a data breach
Organizations must contain the incident, investigate the cause, notify affected individuals, and take steps to prevent future breaches.
Q4. How can organizations prevent data breaches
Implementing strong authentication, encryption, access control, and continuous monitoring helps prevent breaches.
Q5. How does Loginsoft help reduce the risk of data breaches
Loginsoft provides vulnerability intelligence, monitoring, and security engineering to identify risks early and strengthen cybersecurity defenses.
Q6. Is a “data breach” the same as being “hacked”?
Not always. A hack may or may not lead to a breach. A data breach specifically means unauthorized access, exposure, or loss of data. Sometimes a breach is caused by human error or loss of a device, not necessarily a hacking attack.
Q7. Can data breaches happen even without cyber-attacks?
Yes. Data breaches often happen because of accidental exposure, lost devices, misconfiguration, or insider negligence.
Q8. What type of organization can suffer a data breach?
Any small business, global enterprise, government, health care, non-profit. If you store or process sensitive or personal data, you are potentially at risk.