Vulnerability Intelligence Annual Report 2025
Vulnerability Intelligence Annual Report 2025

An Application Programming Interface (API) enables one software system to communicate with another. When an application exposes an API, external systems or clients can request specific services or data from it.
API security focuses on protecting these interfaces from misuse, abuse, and cyberattacks. Just like applications, servers, and networks, APIs are attack surfaces, and because they expose functionality to external parties, they are often attractive targets for attackers.
API security is a critical part of modern web application security. Most digital applications today rely heavily on APIs, and each exposed API introduces additional risk. A helpful analogy is opening a building to the public: while it allows business to function, it also increases the likelihood of unauthorized or malicious activity. APIs work the same way, by allowing outside access, they expand the potential attack surface.
APIs face a wide variety of threats, many of which stem from improper design, weak access controls, or insufficient monitoring. Some of the most common risks include:
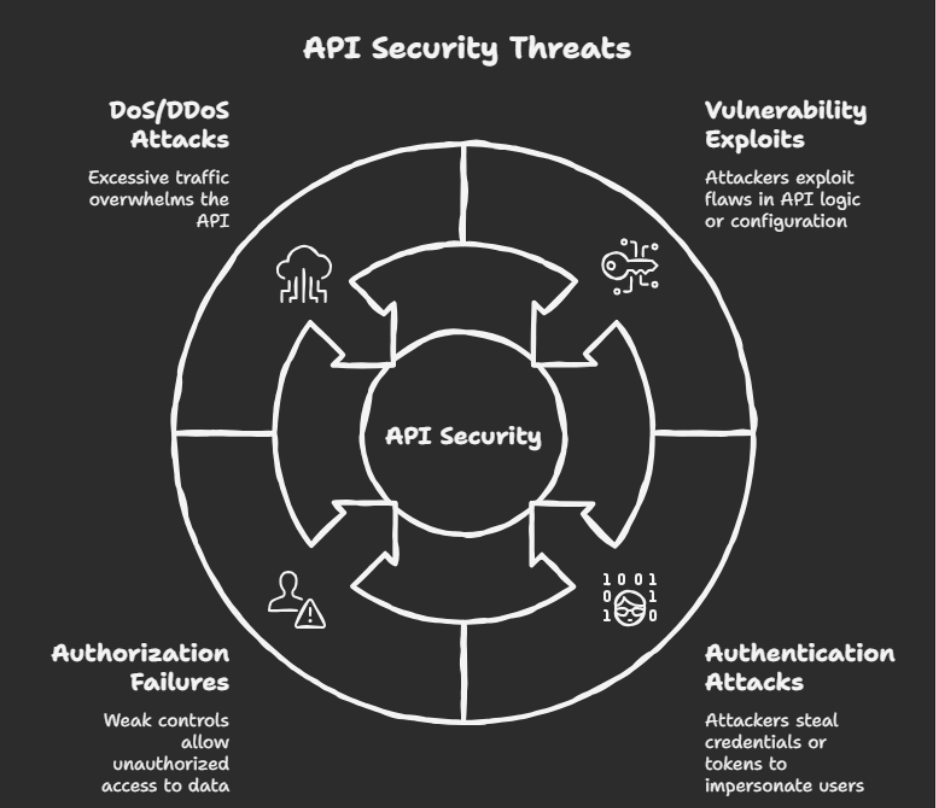
Attackers may send specially crafted requests designed to exploit flaws in an API’s logic or configuration. These vulnerabilities can lead to unintended access or system compromise. Industry groups like OWASP publish lists of the most critical API vulnerabilities, including issues such as injection attacks and security misconfigurations. When an exploit targets a previously unknown flaw, it is considered a zero-day threat, which is particularly difficult to defend against.
APIs typically require authentication to verify who is making requests. However, authentication mechanisms can be compromised if attackers steal credentials, intercept tokens, or obtain valid API keys, allowing them to impersonate legitimate users.
Authorization controls define what authenticated users are allowed to do. When these controls are weak or incorrectly implemented, users may gain access to data or functionality beyond their intended permissions, increasing the risk of data exposure.
APIs can be overwhelmed by excessive traffic, either accidentally or intentionally. In denial-of-service (DoS) or distributed denial-of-service (DDoS) attacks, attackers flood an API with requests to slow it down or make it unavailable to legitimate users.
To mitigate these threats, organizations rely on layered API security strategies such as strong authentication, authorization enforcement, rate limiting, schema validation, and web application firewalls (WAFs).
As technologies like cloud computing and the Internet of Things (IoT) continue to grow, APIs have become the primary way systems exchange sensitive information. APIs often handle credentials, financial data, personal information, and operational controls.
An insecure API can provide attackers with a direct entry point into otherwise well-protected systems. Common attack techniques include man-in-the-middle (MITM) attacks, injection attacks, DDoS attempts, and broken access control exploitation. Securing APIs is therefore essential to protecting the entire application ecosystem.
At its core, an API is simply a mechanism that allows two software systems to interact.
For example, a mobile mapping app does not store global street data locally. Instead, it requests that information from a backend service that maintains up-to-date geographic data. The connection between the app and the backend service is made possible through an API.
Different API architectures introduce different security considerations. REST, SOAP, and GraphQL each require tailored security controls.
REST APIs use standard HTTP methods and resource-based URLs. Common security considerations include:
Securing REST APIs requires a comprehensive approach that addresses each of these areas.
SOAP APIs rely on XML-based messaging and often use protocols such as HTTP or SMTP. Key security practices include:
GraphQL exposes a single endpoint that supports flexible queries, which introduces unique risks:
Because GraphQL allows clients to define exactly what data they retrieve, careful access control is essential.
Modern API attacks typically fall into four broad categories:
Lack of Visibility and Governance
Attackers exploit undocumented, unmanaged, or third-party APIs, often referred to as shadow or zombie APIs, that lack proper oversight.
API Abuse and Misuse
In these attacks, APIs are used exactly as designed, but in unintended ways that result in data leakage or abuse due to weak design controls.
Business Logic Exploitation
Attackers slowly analyze how an API behaves to uncover flaws in business logic, enabling unauthorized access or misuse over time.
Stolen Credentials and Social Engineering
Attackers use phishing or social engineering to obtain valid API credentials, allowing them to operate as legitimate users. A large percentage of API attacks originate from authenticated, but malicious actors.
Industry research highlights recurring API weaknesses, including:
These vulnerabilities underscore the need for continuous visibility and protection.
To reduce API-related risk, organizations should adopt the following best practices:
At Loginsoft, API Security is treated as a high-impact area of cyber risk. Through our Threat Intelligence, Vulnerability Intelligence, and Security Engineering Services, we help organizations identify API threats and reduce exposure.
Loginsoft supports API security by
Our intelligence-led approach ensures APIs remain secure without slowing innovation.
Q1. What is API Security
API Security is the practice of protecting application programming interfaces from unauthorized access and attacks.
Q2. Why are APIs targeted by attackers
Because APIs expose data and business logic directly to the internet.
Q3. What are common API security risks
Broken authentication, excessive data exposure, and API abuse.
Q4. How does API security differ from web security
API security focuses on programmatic access rather than user driven interactions.
Q5. How does Loginsoft help with API security
Loginsoft identifies API threats and enriches detection with threat intelligence to reduce risk.