Vulnerability Intelligence Annual Report 2025
Vulnerability Intelligence Annual Report 2025

Cross-site scripting (XSS) is a web application security flaw that allows attackers to interfere with how users interact with a vulnerable website. It works by injecting malicious client-side code, usually JavaScript, into trusted web pages, which then execute in a user’s browser.
XSS exploits weaknesses in how applications handle user input and output, allowing attackers to bypass the same-origin policy, a browser security control meant to isolate websites from one another. When an XSS vulnerability is exploited, attackers can impersonate legitimate users, perform actions on their behalf, and access sensitive data such as session tokens or personal information.
XSS occurs when a web application includes untrusted input in its responses without proper validation or sanitization. As a result, malicious scripts are sent to users and executed by their browsers under the assumption that the content is safe.
Because the code runs in the context of a trusted website, the browser allows it to access session data, cookies, and other sensitive resources, giving attackers a powerful foothold.
XSS vulnerabilities are typically grouped into three main categories.
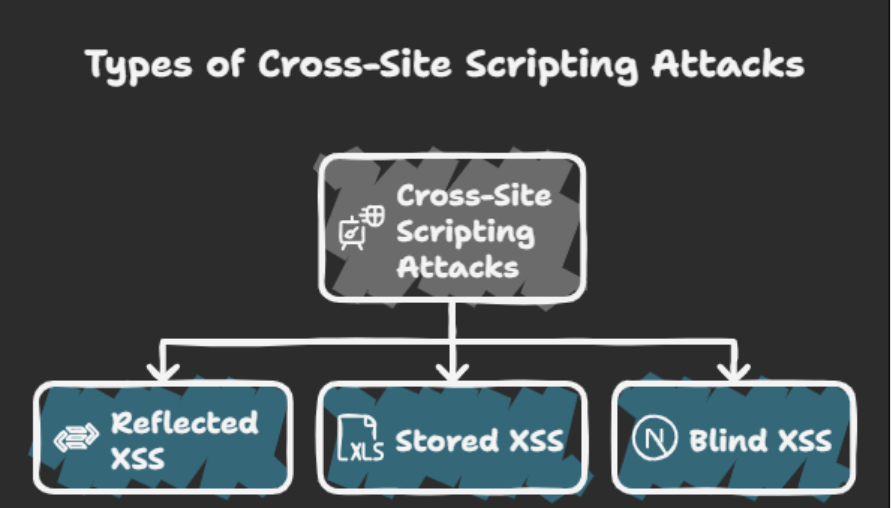
Reflected XSS occurs when malicious input is immediately returned by the server in a response, such as in error messages or search results.
The attack is usually delivered through:
When a victim clicks the link or submits the form, the payload is sent to the vulnerable server and reflected back in the response. Because the response originates from a trusted site, the browser executes the script.
Reflected XSS happens within a single request–response cycle and does not store the payload on the server.
Stored XSS happens when malicious code is permanently saved on the server-commonly in databases, comment sections, message boards, or user profiles.
When users later view the affected content, the stored script is delivered and executed in their browsers. This type of XSS is especially dangerous because it can impact many users without additional attacker interaction.
Blind XSS is a form of stored XSS where the attacker cannot immediately see the result of the injection. Instead, the payload executes in a backend or administrative interface.
A common example is a feedback form where malicious input is saved. When an administrator later views the submission through a backend system, the payload runs. Because the execution happens outside the attacker’s direct view, confirmation is difficult and often requires specialized detection tools.
JavaScript-based XSS attacks are particularly powerful because JavaScript can access sensitive browser resources.
Attackers can use XSS to:
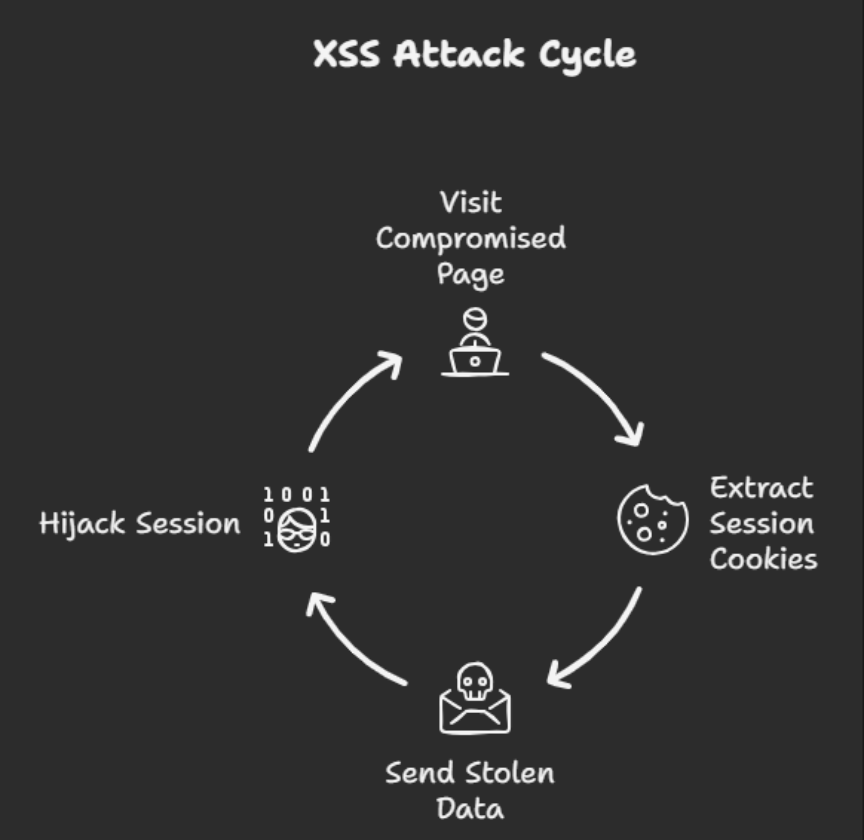
Cookies act as temporary authentication tokens, allowing users to remain logged in. If stolen, they can be reused to impersonate victims without requiring passwords.
XSS attacks can have serious consequences for both users and organizations. Even a single vulnerable page can expose thousands of users.
XSS matters because it
XSS is one of the most common web vulnerabilities.
There is no single solution for XSS prevention. Effective protection requires multiple layers of defense tailored to the application.
Where possible, prevent users from submitting raw HTML. Safer alternatives include markdown or controlled rich-text editors that limit allowed formatting.
Input validation ensures submitted data matches expected formats. For example:
Sanitization removes or neutralizes malicious code before content is rendered in the browser. This step is especially important for user-generated content stored on the server.
Applications can reduce the impact of XSS by:
Despite being a well-known vulnerability, XSS remains prevalent due to complex applications and frequent updates. Modern frameworks help reduce risk, but misconfigurations and custom code can still introduce XSS flaws.
Continuous testing and monitoring remain essential.
At Loginsoft, Cross-Site Scripting is treated as a critical application security risk. Through our Vulnerability Intelligence, Threat Intelligence, and Security Engineering Services, we help organizations detect and reduce XSS exposure.
Loginsoft supports XSS defense by
Our intelligence-led approach ensures XSS vulnerabilities are addressed before attackers exploit them.
Q1. What is Cross-Site Scripting?
Cross-Site Scripting is a vulnerability that allows attackers to inject malicious scripts into web pages viewed by users.
Q2. Is XSS a client-side or server-side attack?
XSS executes on the client side but is caused by server-side input handling issues.
Q3. What are the main types of XSS?
Stored, reflected, and DOM based XSS.
Q4. How dangerous is XSS?
XSS can lead to session hijacking, data theft, and phishing.
Q5. How does Loginsoft help prevent XSS?
Loginsoft helps identify XSS risks and prioritize remediation using intelligence-driven security analysis.